Privacy apps I use to run my business
Privacy on the Computer
Imagine going to bed without locking your front door, closing the downstairs windows, or drawing the curtains. If you were robbed in the night, it would be fair to say that you bear some responsibility for not taking basic precautions. So why do most owners of computers, phones, and tablets lack a checklist for keeping themselves safe in what is arguably the most adversarial environment mankind has ever created?
4 Levels of Privacy
I appreciate how Eric, the privacy expert, explains the different degrees of privacy:
- Level 1: This includes the majority of users who turn on their new phone or computer, use pre-installed browsers, search engines, and apps, and jump onto social media without asking any questions.
- Level 2: This group consists of the privacy-aware individuals, like me. We use tools such as Proton Mail, Firefox, and some open-source apps. We prefer Nostr over Twitter and ensure we have data backups of our hard drives. Generally, we are not happy with how the entire internet apparatus is designed to trawl the unaware among us for every data point that corporations and overreaching government departments can find, use, or sell.
- Level 3: Activists fall into this category. They use the Tor browser, operate under pseudonyms online, and prefer cryptocurrency over traditional bank accounts.
- Level 4 are being hunted by the 3 letter agencies. People like Edward Snowdon who shouldn't even be online.
Three basic options to stay secure and protect your privacy.
1 - Stay offline
This may seem impractical, but it is arguably the best security step you could take. Consider using an old iPhone or a Linux laptop to store your private information—just in case. If it’s never connected online and has a decent password, what could go wrong? This tactic is often recommended by security experts who understand the risks. Reports suggest that an iPhone without a SIM card is one of the most secure devices on the market.
2 - Use air-gapping with hardware devices.
In this approach, your online device is connected to a sensitive data storage device that is never online and is protected by encrypted key pairs. To visualize this, think of a laptop paired with a Bitcoin hardware wallet or signing device, such as CoinKite, Trezor, or Ledger. These devices are remarkably effective for those of us who may not be technically savvy, providing a way to protect data. The contents of a Ledger, for example, never appear online, yet they can communicate with your online computer to facilitate transactions. With this air-gap approach, the contents of the hardware wallet remain safe from online hacks.
However, it’s important to note that hardware wallets are not automatically impregnable. If they are not set up with all available layers of protection—such as a passphrase and seed phrase—then a skilled hacker with physical access and relatively low-cost hacking tools could potentially compromise them. There was a big hoo-hah when someone claimed they managed to break into a Trezor device, for example. But follow the set-up instructions and you can sleep well.
3 - Use a Secure Online Service Like Nostr
Nostr employs encryption and key pairs to protect your data, following the same principles of air-gapping and encryption mentioned earlier. The key difference with Nostr is that, for convenience, the entire encryption/decryption process typically occurs within your phone's or computer's browser. While this approach offers a lower level of protection compared to dedicated hardware signers that are separate from your device, it still provides robust security under normal circumstances.
You can enhance your security further by using the Amber Event Signer app, which keeps your keys on your phone rather than in the browser app.Having ventured into the realms of Nostr and Bitcoin, where privacy and encryption are paramount,
I have become increasingly aware of the privacy protections we could have compared to what we currently experience. For instance, whenever I visit a website that requests my username and email address along with a password, I genuinely worry that they do not prioritize my security. Banks, are you listening?
Are all bets off if you lose your phone or laptop?
Fort Knox on your phone is fine—until you lose your phone. However, there are several steps you can take to protect your device, even if it falls into the hands of a thief.
Protect your device with a strong password.
A 30-character password will keep most casual thieves occupied forever. However, a hacker who knows how to reboot a computer in a certain way can reset the master password in no time and access everything on your hard drive.
- Encrypt your hard drive.
- For Mac users, FileVault is built in.
- For Windows just turn on Bitlocker
- For Linux, old Windows or non Pro Windows and Mac consider Veracrypt
- For iPhone check these instructions Remember, your back-up on iCloud cannot be encrypted
- For Android phones here's the info you need.
- For USB drives, encrypt this way.
- Hard drive back-up
- Best strategy is to assume you won't see your lost or stolen device again.
- Keep a copy of your encrypted hard drive far from your favourite phone or laptop at home.
- If you use the Cloud, make especially sure your backup is in an encrypted folder. Proton Drive is a good option as everything on their Cloud is encrypted by default.
- Use a password manager, but keep it on a separate device, such as a pen drive
You have a password manager, right! This review of Bitwarden a free and reliable app will get you started. Having said that, a browser-based password manager won't help if the computer or phone is stolen! Therefore the next level up in password manager security is to keep your passwords on a separate hardware drive. That could be on a PC external hard drive or a pen drive.
- Made easy with an Only Key Passwordless entry to:
- your computer
- your encrypted drive
- most websites with 2FA (Two factor authentication).
- Harder method is to make your own pen drive password storage device
Password managers can list everything, not just for your online life, but for real life too — such as library cards, gym memberships. If you want to take all that with you on a pen drive
- install Windows on a USB drive or
- Linux on a USB drive or
- Mac OS X on a flash drive
then install a Password Manager.
- Keep a handy list on paper
- Not a list of passwords but emergency numbers to call to block bank accounts and so forth if the details are on your lost or stolen device. (14 things to do if you lose your wallet.)
Tracker Apps and Location Services
While tracker apps like Find My... and Prey can help you locate a stolen device, and even disable phones or laptops from distance, they also raise concerns about personal privacy. Consider the risks and benefits before using these services. There are real world safety ramifications when we prioritise finding lost phones over maintaining personal privacy.
"Many reports have shown how criminals have used Apple AirTags to track, stalk, and harm others."
Google are trying to use Bluetooth on billions of phones to aid with tracking "lost" phones. But obviously each phone is in a human's pocket, raising serious privacy questions.
Think about what that means if a Find My Device option from Apple or Google has already been installed in the factory. There is a direct line between the manufacturer and the owner. Additionally, it's important to note that the latest revelation indicates that Airplane Mode doesn't actually turn off your phone's Wi-Fi. This leaves you vulnerable to being tracked by triangulation, even if there is no SIM card in the device.
*It's not even a recent revelation! The issue regarding Airplane Mode not completely disabling Wi-Fi has been discussed for several years, but it gained more attention in 2016 when security researchers and privacy advocates began highlighting the potential vulnerabilities associated with Airplane Mode.
If you do go the Find My... route, these are the options
Find my... apps
- iPhone and Mac - Find My app will disable and track your device. Older devices look here
- Android - Find My Device is for you.
- PC with Windows 10 or 11 has a Find my Device option too.
- Find your X-Box!
- How to track your Linux PC. It was this link that made me pause for thought. It is asking me to willfully install a tracker into the innermost depths of my computer. Installing a Find My Device option at the Apple or Google phone factory is surely a trivial task.
Nostr and Privacy
Nostr is a service that prioritizes user privacy. Interacting with privacy conscious developers and enthusiasts has prompted me to question the privacy levels of other parts of my web and computer set up.
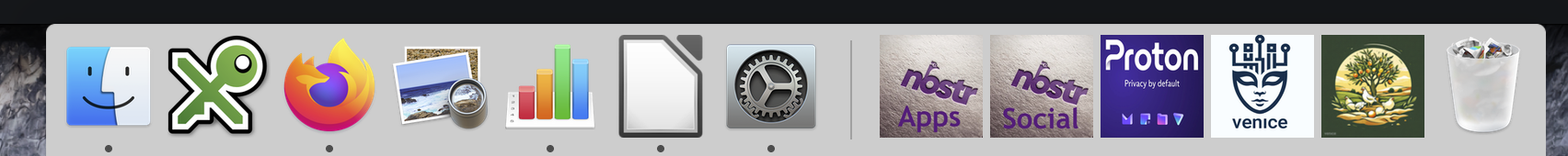
The Privacy Dock from left to right.
Let me preface this section with: Changing from Mac OS to Linux would be a big jump in privacy straight out the traps. It's on my to-do list.
For now, here's a look at my personal Mac setup. The choice of app is based on prioritizing my privacy and security up to my current level 2 of "privacy-awareness"!
- Password manager, KeepassX, is offline and encrypted.
- A privacy-first browser, Firefox. More on improving Firefox's default privacy.
- A convenient image viewer and PDF editor called Preview. I'm aware of its aptitude for metadata generation, so I use ImagOptim to strip metadata before posting images online.
- LibreOffice (Open Source version of Word) and lately CotEditor as my offline notepad and document writers.
- I save some documents as password-protected PDFs (Export as PDF) and store them on Proton Drive.
- System Preferences are full of privacy-breaking utilities. Dictation literally phones back to Apple!
- Bluetooth is secure through obscurity when I am out in the countryside.
- A suite of Nostr clients are secure by default
- Proton's encrypted email, drive, and collaborative docs/notes services.
- A Proton VPN shields my IP and doesn't slow down my browser. The VPN alone is a very effective privacy protection method, like a big wall of privacy first. See the following outline of Proton to understand why.
Proton Suite
Proton is a Swiss company that offers a suite of encrypted services, including email, drive, notes, and calendar, enabling users to get work done without needing a triple Computer Science degree. While the content encrypted on the server is immune from snooping hackers and Proton does not possess the key to decrypt email content, the service is not resistant to state attacks on user privacy.
Proton receives over 6,000 demands from Swiss law enforcement each year to hand over user details, and they comply in most instances. An article which arose from a French activist being "shopped by Proton" to the Swiss authorities, explained that Proton is obliged to hand over IP addresses if a law has been broken. Proton's solution is to suggest using the Tor browser so that IP addresses are never exposed to them in the first place, leaving them nothing to collect, nothing to hand over. A VPN would achieve the same result.
- Encrypted email.
- Drive, encrypted cloud-based file storage.
- Encrypted notes and collaborative document sharing
- Encrypted calendar
- VPN that doesn't seem to slow down your browser
- Pass, an encrypted password manager for completing online forms.
- Bitcoin Wallet. Their Proof of Work to demonstrate full commitment to privacy and self sovereignty.
To be fair, it is the most universal and easiest to use end-to-end encryption chat app between individuals - with a couple of caveats.
1 - I don't use it for business.
...any content shared with a business on WhatsApp will be accessible by “several people in that business.”... Moreover, businesses may work with third-party service providers to manage communications with customers. Such providers might also include Facebook. Source
2 - I am aware that Whataspp conversations are only 100% secure, if you check the option to encrypt your Whatsapp chat archive. Archives are stored on Google Drive or iCloud and if left unencrypted, every private conversation can be read by Google or Apple, or their approved contractors.
Simplex a business message app built on extreme privacy
This is the app that I will try to use to notify my customers the day before I deliver eggs to their village. Simplex chats are completely private and it offers the choice of complete anonymity if required.
Two-Factor Authentication
I use two-factor authentication (2FA) to add an extra layer of security to my online accounts. These rely on Authenticator apps, which generate random numbers to match before accessing an app. Here's a bunch of Google authenticator alternatives. But they are a security hole in themselves.
Is there more?
If you want to graduate to level 3 activist privacy level and beyond, there are way more areas to discover, including: no 2FA, OTP email, eSMS with Efani, backup codes if you lose your phone, Google Titan or Yubikey... DeGoogling your phone, your office suites, Librebooks and Linux, and so the list goes on.
Securing a comfortable degree of privacy is a worthwhile mission, just realise an endless battle is being waged to find out more about you than ever before. There is always a compromise between security and convenience and personally I think the aim is to use Open Source software, Operating Systems and hardware that has been designed and run by cleverer people than us to try achieve that balance in their products.
Word to the wise
There are so many sharp minds fighting for rights to privacy. There are so many activist developers trying to break the stranglehold that Google, Apple, FaceBook and co have been exerting. And they are just three of many who don't have such a high profile. Oracle CEO, Larry Ellison, bragging about their databases compared to FaceBook, before he was nailed with a $115m fine:
in our data cloud, marketers are able to target consumers and do a much better job of predicting what they’re going to buy next. I believe five billion consumers are in our identity graph – five billion.
And we haven't even started with the data that Governments are accumulating. As Snowden points out, there is a fundamental issue to address - why is a Government even able to access so much personal data that legally it is not entitled to collect itself?
The U.S. government, in particular, is acting on the basis of a tenuous ruling that the people do not own the data collected on them by often monopolistic third-party entities. These entities frequently leave their customers or users with no choice but to accept privacy-intrusive terms and conditions. Subsequently, the government—of the people—takes that data for its own overreaching purposes, such as silencing political opponents, human rights activists, and even groups of campaigning mothers.
The damage being caused now is significant, and even more harm is being stockpiled for the future when the vast banks of data can be sorted and analyzed by AI-powered analytics. You might think you have nothing to hide, but I’m sure someone is already writing a documentary—or perhaps a Hollywood blockbuster—about an overreaching government department using Minority Report-style technology to mine data and hold people accountable for actions they took at the age of eight.
Privacy-respecting groups are building alternative internet platforms, not asking permission from governments causing the problem. Big Brother Watch is one example of citizens taking the UK government to task over data collection - facial recognition surveillance at an industrial scale. Interesting to see a bipartisan bill proposal in the US of all places, where representatives from both sides are joining forces to introduce a GDPR style privacy law putting users' interests ahead of corporations or government interests. Because you know what the collusion between corporations and government truly defines, right?!

